Architecture Of IOT :
There is no single and general understanding about the design of IoT that is settled on by the entire world and specialists. Numerous and various models have been proposed by scientists. As per a few scientists, IoT engineering has three layers, however a few specialists support the four-layer design. That's what they feel, because of improvement in IoT, the design of three layers can't satisfy the prerequisites of uses. Because of a test in IoT with respect to security and protection, the design of five layers has likewise been proposed. It is viewed as that an as of late proposed engineering can satisfy the necessities of IoT in regards to security and protection.
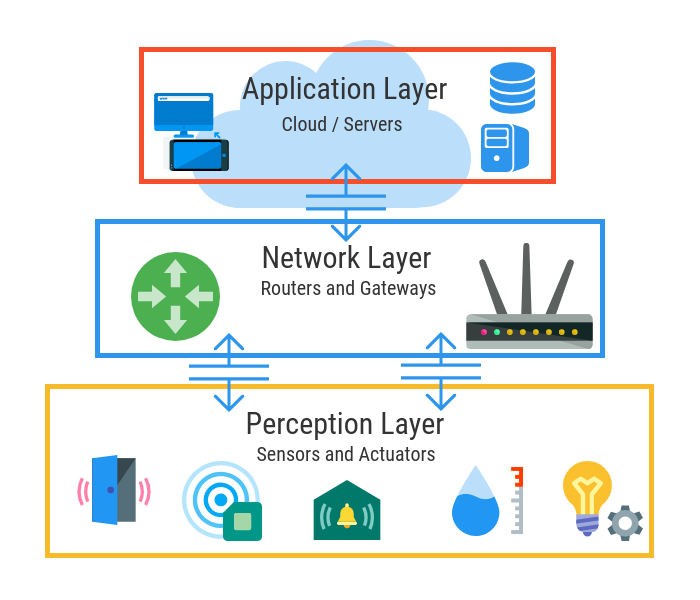
Perception layer :
It is otherwise called a sensor layer. It works like individuals' eyes, ears and nose. It has the obligation to recognize things and gather the data from them. There are many sorts of sensors connected to objects to gather data, for example, RFID, 2-D scanner tag and sensors. The sensors are picked by the prerequisite of utilizations. The data that is gathered by these sensors can be about area, changes in the air, climate, movement, vibration, and so forth. Nonetheless, they are the principal focus of assailants who wish to use them to supplant the sensor with their own. Consequently, most of dangers are connected with sensors [35-37]. Normal security dangers of discernment layer are:
Eavesdropping:
Listening in is an unapproved continuous assault where confidential correspondences, for example, calls, instant messages, fax transmissions or video gatherings are caught by an aggressor. It attempts to take data that is sent over an organization. It exploits unstable transmission to get to the data being sent and gotten.
Node Capture:
It is one of the risky assaults looked in the discernment layer of Parcel. An aggressor deals with a key hub, like an entryway hub. It might release all data including correspondence among source and recipient, a key used to make secure correspondence and data put away in memory [38].
Fake Node and Malicious:
It is an assault wherein an assailant adds a hub to the framework and information sources counterfeit information. It expects to quit communicating genuine data. A hub added by an aggressor consumes valuable energy of genuine hubs and possibly control to obliterate the organization.
Network layer:
Network layer is otherwise called transmission layer. It behaves like a scaffold between discernment layer and application layer. It conveys and communicates the data gathered from the actual articles through sensors. The vehicle for the transmission can be remote or wire based. It additionally gets a sense of ownership with interfacing the brilliant things, network gadgets and organizations to one another. Accordingly, it is exceptionally delicate to assaults from the side of aggressors. It has conspicuous security issues with respect to trustworthiness and validation of data that is being moved in the organization. Normal security dangers and issues to organize layers are
• Denial of Service (DoS) Attack:
A DoS assault is an assault to keep valid clients from getting to gadgets or other organization assets. It is commonly achieved by flooding the designated gadgets or organization assets with excess solicitations in a request to make it unimaginable or hard for some or all bona fide clients to utilize them [41].
- Main-in-The-Middle (MiTM) Attack:
MiTM assault is an assault where the aggressor subtly captures and modifies the correspondence among source and recipient who accept they are straightforwardly speaking with one another.
Since an aggressor controls the correspondence, thusly the individual can change messages as indicated by their requirements. It makes a serious danger online security since they give the assailant the office to catch and control data continuously [42].
- Capacity Assault:
The data of clients is put away on stockpiling gadgets or the cloud. Both capacity gadgets and cloud can be gone after by the aggressor and client's data might be changed to mistaken subtleties. The replication of data related with the entrance of other data by various sorts of individuals gives more opportunities to assaults.
• Take advantage of Assault:
An endeavor is any improper or unlawful assault in a type of programming, pieces of information or a grouping of orders. It exploits security weaknesses in an application, framework or equipment. It ordinarily accompanies the point of overseeing the framework and takes data put away on an organization [43].
Application Layer:
Application layer characterizes all applications that utilization the IoT innovation or in which IoT has conveyed. The uses of IoT can be savvy homes, shrewd urban areas, brilliant wellbeing, creature following, and so on. It has the obligation to offer the types of assistance to the applications. The administrations might be shifting for every application since administrations rely upon the data that is gathered by sensors. There are many issues in the application layer in which security is the central question. Specifically, when IoT is utilized to make a shrewd home, it presents numerous dangers and weaknesses from within and outside. To carry major areas of strength for out in an IoT based brilliant home, one of the main pressing concerns is that the gadgets utilized in shrewd homes have frail computational power and a low measure of capacity, for example, ZigBee [44]. Normal security dangers and issue of use layer.
• Cross Site Prearranging:
It is an infusion assault. It empowers an assailant to embed a client-side content, for example, java script in a believed site saw different clients. Thusly, an assailant can totally change the items in the application as per his necessities and utilize unique data in an unlawful manner [45]
.
• Noxious Code Assault:
It is a code in any piece of programming expected to make undesired impacts and harm the framework. A kind of danger may not be hindered or constrained by the utilization of hostile to infection instruments. It can either enact itself or resemble a program requiring a client's thoughtfulness regarding play out an activity.
• The capacity of managing Mass Information:
Because of an enormous number of gadgets and a gigantic measure of information transmission between clients, it has no capacity to manage information handling as per the necessities. Accordingly, it prompts network aggravation and information misfortune.